-
• #2
...there is a bit more needed to understand which part of it you need help with... such as: what did you and could do successfully, what avenues you went down to - literally - go down, and where and with what are you stuck right now /:
-
• #3
I try so:
SPI3.setup({ mosi:B5, miso:C11, sck:C10 }); var eth = require("WIZnet").connect(SPI3, D0); eth.setIP({ip : "192.168.1.13",subnet : "255.255.255.0",gateway:"192.168.1.1",dns:"192.168.1.1"}); var WebSocket = require("ws"); const ws = new WebSocket('echo.websocket.org', { port: 80 }); ws.on('open', function() { console.log('opened'); ws.send("hello world"); }); ws.on('message', function(message) { console.log('received: ', message); });how to use WSS correctly?
ws = new WebSocket('wss://echo.websocket.org', { port: 443 });???
-
• #4
What board are you on?
-
• #5
Thr 2018.11.08
@Wilberforce, I'm going to side with you on this, start with the board type.
But, isn't it as simple as in Line 1 setup?
SPI3.setup({ mosi:B5, miso:C11, sck:C10 });When I played with Espruino Original, Pico and Wifi, for hardware SPI, wasn't the SPI requirement that all pins had to stay with the same SPI designation?
and, when one checks the board pinouts, @Gordon did a fantastic job on establishing a firm naming convention, and keeping it consistent. e.g. A pins with SPIn for instance
Unless the non-Espruino boards have a different labeling requirement, seems to be a good place to start.
@MaksR please post the board type and verify with the online docs about SPI pin designation.
If that doesn't solve the issue would you please post some output as in the paths tried, as @allObjects pointed out. It is extremely difficult for those willing to expend their valuable time to assist without some basic foundation to work with.
'help with the Websocket security client example'
Were you working from an online snippet perhaps and would you please post that link?
'how to use WSS correctly?'
Are you asking if this is the correct syntax to set up a
WebSocket, perhaps? -
• #6
Board: STM32F4DISCOVERY + W5500 NET
Library "crypto " added to firmware (mbedtls).
SPI interface works!
Using WS and 80 port I get a response from echo.websocket.org "hello world"
Also I tried to connect to https server. It works!
butws = new WebSocket('wss://echo.websocket.org', { port: 443 });does not work!
may be incorrect syntax or something?
-
• #7
Ok, I think the issue is that by default the WebSocket example just uses the
netlibrary to initialise a connection, nottls: https://github.com/espruino/EspruinoDocs/blob/master/modules/ws.js#L94So ideally changing the library to do this:
WebSocket.prototype.initializeConnection = function () { require("tls").connect({ host: this.host, port: this.port }, this.onConnect.bind(this)); };would probably work. Unfortunately the way it's done (not actually exporting
WebSocketitself) means that you can't actually modify just that function when loading in the library - you'd have to copy the module, change it, and load it in yourself. -
• #8
Thank you!
what to do with mbedtls_ssl_handshake returned -0x7 ? -
• #9
Handshake from Wireshark:
Espruino - Client Hello:TLSv1.2 Record Layer: Handshake Protocol: Client Hello Content Type: Handshake (22) Version: TLS 1.0 (0x0301) Length: 49 Handshake Protocol: Client Hello Handshake Type: Client Hello (1) Length: 45 Version: TLS 1.2 (0x0303) Random: 30de5c92dbfd4ddcb00fa82fed023683b8b899788e0e189e... GMT Unix Time: Dec 25, 1995 11:10:58.000000000 RTZ 2 (зима) Random Bytes: dbfd4ddcb00fa82fed023683b8b899788e0e189e3b5f5a72... Session ID Length: 0 Cipher Suites Length: 6 Cipher Suites (3 suites) Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA256 (0x003d) Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA256 (0x003c) Cipher Suite: TLS_EMPTY_RENEGOTIATION_INFO_SCSV (0x00ff) Compression Methods Length: 1 Compression Methods (1 method) Compression Method: null (0)Tomcat 9.13 - Handshake Failure:
TLSv1.2 Record Layer: Alert (Level: Fatal, Description: Handshake Failure) Content Type: Alert (21) Version: TLS 1.2 (0x0303) Length: 2 Alert Message Level: Fatal (2) Description: Handshake Failure (40)Maybe the problem is due to version: TLS 1.0 (0x0301)?
or Random (GMT Unix Time)?
or Cipher Suites ? -
• #10
Maybe you could try providing pre-made certs when you connect? http://www.espruino.com/Reference#l_tls_connect
-
• #11
Referring to #7
I tried this on the Linux build and there was no -x07 error
-
• #12
in module wss.js:
function WebSocket(host, options) { this.socket = null; options = options || {}; this.host = host; this.port = options.port || 80; this.protocolVersion = options.protocolVersion || 13; this.origin = options.origin || 'Espruino'; this.keepAlive = options.keepAlive * 1000 || 60000; this.masking = options.masking!==undefined ? options.masking : true; this.path = options.path || "/"; this.protocol = options.protocol; this.lastData = ""; this.secWebSocketKey = buildKey(); this.cert = options.cert; this.key = options.key; this.ca = options.ca; this.connected = false || options.connected; this.headers = options.headers || {}; } WebSocket.prototype.initializeConnection = function () { require("tls").connect({ host: this.host, port: this.port, ca: this.ca, cert: this.cert, key: this.key }, this.onConnect.bind(this)); };Espruino code:
SPI3.setup({ mosi:B5, miso:C11, sck:C10 }); var eth = require("WIZnet").connect(SPI3, D0); eth.setIP({ip : "192.168.1.13",subnet : "255.255.255.0",gateway:"192.168.1.1",dns:"192.168.1.1"}); //ininodeku.herokuapp.com //echo.websocket.org var WebSocket = require('wss'); const ws = new WebSocket('93.183.80.194', { path: '/time/ws', port: 8443, protocolVersion: '13', protocol : "chat", // optional websocket protocol origin: '', // keepAlive: 60, // Ping Interval in seconds. // headers:{ some:'header', 'another-header':42 } // optional websocket headers ca: atob("MIIFaTCCA1GgAwIBAgIJANSBTFhEm7iTMA0GCSqGSIb3DQEBCwUAMEsxCzAJBgNVBAYTAlJVMQ8wDQYDVQQIDAZSdXNzaWExEzARBgNVBAoMCkxvZ2ljaG91c2UxFjAUBgNVBAMMDUxvZ2ljaG91c2UgQ0EwHhcNMTYxMDA0MTkxNDEzWhcNMjYxMDAyMTkxNDEzWjBLMQswCQYDVQQGEwJSVTEPMA0GA1UECAwGUnVzc2lhMRMwEQYDVQQKDApMb2dpY2hvdXNlMRYwFAYDVQQDDA1Mb2dpY2hvdXNlIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAmIc8oR9feUtXztaQQBnwMkXoIjGb6+6DIADk/J/VflTOYk6tinj0Si7+3jAYrHjUZHGDTvTa52In10xcat5h9oW8hy3PekmbO2/C88zh/gbcgX5O7StvU3PWk4TdVTJk+Y3stxajBgEvrh+CXmb+iztmFltG7ySbyqifa4LTkVq2udmsBcQAScaUd7EZ3/ZZejd9ShzzHpnA58s9YW1j+DdQ+GAwxfYB6LhvtRpkrybDoPVWgJDbl7Q4WuOcx56+MhjQMbzRM2K9vWOzZns/Un0YZe6rokDjurXuOpOsp9IzVkK9lE2jeqDQRkf4RxiFy5vEuZRjpx7haZAajeNevoG28RwKe64VDsYHQCgQcs7VRXokvPnrCgAlRpeZmIpVWHxb8xR3+VU0cw+DIg75nQBf74KfPmCyhhVAvsN3ljC9rb9Rzf8/X4mMBP15JJk5v9EgXUqmSiYfSTSfGYl6J9jiJW3wNtf48v2DRVw83KI1NjVi3RkYkACayqEupk1cIDNKvHP0Vdh0L+JeHNGXHPK/LwtOomVF8j9u5tr9hjoIf12luA8vbSxSpTBRRpuV3IGAzl268c92Uh0wzNUmsfBz3aZY/+PvFRXFiIljiHFKL/Wq0eJKjtBJZZxckJpBWgYUUR18YvR+JMRMpwIMNfLjkgGmxyPbsbSkfD+vsr8CAwEAAaNQME4wHQYDVR0OBBYEFKT60m+kotmyktFFsy9Weikad/pMMB8GA1UdIwQYMBaAFKT60m+kotmyktFFsy9Weikad/pMMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggIBAImZKZ/nuT/UtZf/9PLKmVDcH3hi5qt0bYZ6BNJ66smpA5XyJOInMzapHmuqPYObj7Yk52qfDOLWrVEHddf29rwkiVQcgriYt9HHZNBF8AdkK5fglDN1jUPpPRUG64iewXM31WizMN7bSlAqeManYui2rw9bvqSDpkt9HTVHY+bbdH1t0DJIo7sm1uTJefugfZC9EoIW3Qtt8ErBdpPimerN7CAQiNXuaBh9JOafEZFUkWIdp4O9oEGkn6oHTeyhaTaZ+Na3sTUIvCTgPRcJO8GwZHCbE27mXeN/aycTrMxFJfFvp7F5zv8vKsbhQqkxpye2YrKeeIxOt8vA8MS/hRiHhBCE4dRo34QV61U5R/TyaDJkHuhLPfKH6+80ZNE7fMdSJQCfcd1ySPcCrrwmeaXf9gZ6YgtgFJjSKArYsBv4/ChVf3U7q6bI5anUdluol69jc0lbNUzV3o/FQVgAxcY/BM171SFEqKlriLmeAyJSBH/ovfHhGp1mIQiHs9KOtibS079tXALP4hORUHFmsk1rDdqSJ0GdkRgbbEkecJLOTa5nmeriSZ6CaOcA9vPdpQxb36fZvZL9KfqzsraoNIOM3TDXTOJ3kCOvlF3g3t2gamJxNgw6wSZW2R/1sRvJvXm99r3V0uUq9dMTLZ6DB2fdhzJ14a2xYwlVtvwpbibG") }); ws.on('message', function(message) { console.log('received: ', message); }); ws.on('close', function() { console.log("Connection closed"); });93.183.80.194 - real ip with Tomcat 9.0.13 and websocket (wss://93.183.80.194:8443/time/ws) + server.crt sign ca
Espruino error: mbedtls_ssl_handshake returned -0x7780.
Wireshark shows that the stage of certificate exchange is not coming !? (I'm not sure).
Tomcat responds with Handshake Failure.Сan tomcat not like Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256 ?
But Espruino is connected to the node.js server! (certificates are the same) , node.js client and browser connects to Tomcat.
1 Attachment
 allObjects
allObjects MaksR
MaksR Wilberforce
Wilberforce Robin
Robin Gordon
Gordon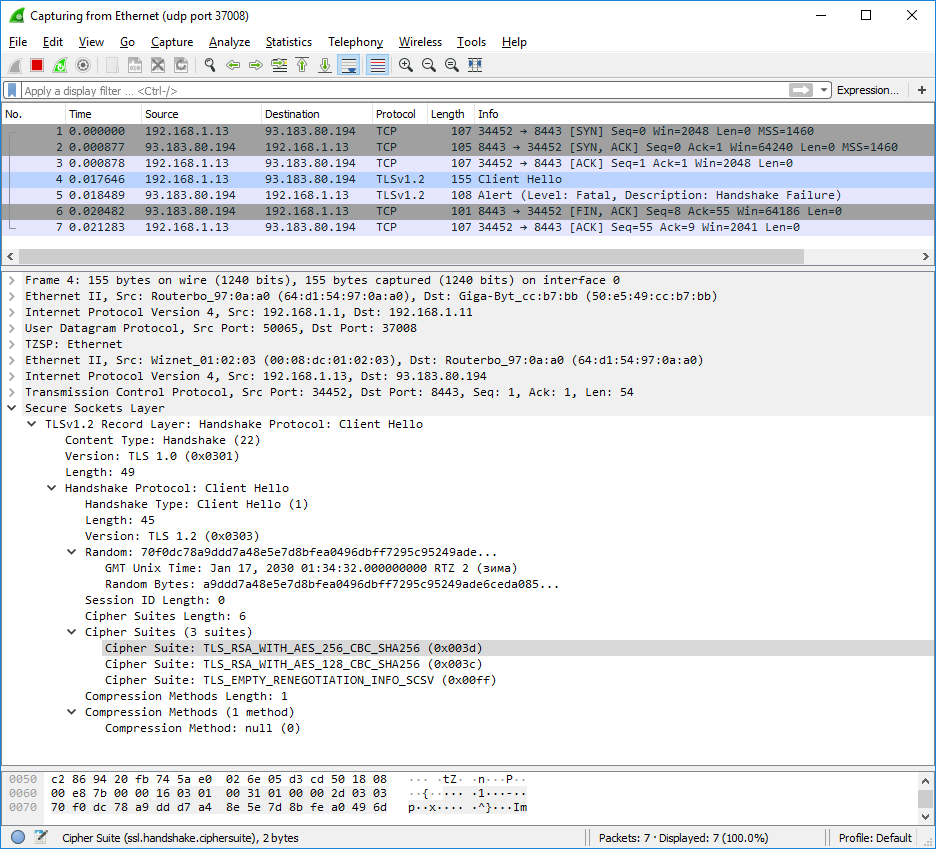
Hi! help with the Websocket security client example.