Smart rings with nrF chips #3354
Replies: 22 comments
-
|
Posted at 2024-02-21 by @fanoush interesting but that one is over usd50 for me, here it is possibly same one for half https://www.aliexpress.com/item/1005006467962445.html |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by @gfwilliams Wow, those look really cool.
I've wondered about this - I know atc1441 has a 'glitcher' for nRF52 that can allow you to read out the firmware of locked devices: https://github.com/atc1441/ESP32_nRF52_SWD The private key won't be in the DFU firmware, but I assume that if you could basically take one apart by destroying it (melt the case off with acetone?), and then read the firmware using the glitcher, you could find the public key - and then maybe you could brute-force it on a PC to ensure that you got an initdata packet that fooled the bootloader? But the hash looks like it's 256 bits (at least) so maybe that's not an option. Thinking about this, as far as I can tell it's only the initData packet for DFU that has microecc run on it (not the whole firmware?), and that packet just contains the size and CRC of the actual firmware, so actually, if you:
You should be good? The CRC computation is pretty simple ( Also, I'm not sure if it's relevant but microecc had a security flaw in it (https://nvd.nist.gov/vuln/detail/CVE-2020-27209) and the one in the ring's firmware almost certainly got that flaw. |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by @gfwilliams Just to add to this: It looks like the whole firmware is checked with microecc (in However, and @fanoush maybe you have some thoughts here because I think you've looked into this in more detail, but an nRF52832 band almost certainly only has 1 flash bank so it has to overwrite the existing app even before that ECC check. So when you do a firmware update, this should happen?
So really it depends whether |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by @fanoush Yes had same ideas but found out it is about finding SHA256 collision = different binary having same hash that is signed in init packet. this currently takes more time than the universe exists, or you get lucky and win a lottery. init packet is signed so it must stay as it is and part of it is sha256 hash of whole binary - at least that is the core idea behind it, looks solid |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by @fanoush Yes you can write modified data there as the sha256 hash is checked after it is all written, but then it will mark it invalid and won't execute it. So either you have bricked device sitting in DFU waiting for correct package or with dual banked update (when there is enough space) the new invalid code is sitting in empty space above the real application waiting for you to jump into it via some clever exploit of original application over BLE |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by user149759 Thanks for sharing your thoughts. How about reaching to the manufacturers and ask for a custom firmware with Espruino? Like bagngle.js may be several people will be interested in this. |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by @fanoush
I think that so far there are exactly zero cases out of many tries where it worked like this before (including both bangle.js watches). But maybe next time. But still, if you can spare the money, get it and take it apart than that is still something that could be interesting. At least we would know there is indeed nrf52 chip inside. |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by @gfwilliams
Ahh, thanks - that's a shame then. I was hopeful that maybe by not actually sending the 'finish' command and disconnecting we could skip the validation step at the end - but I'd imagine that it almost certainly invalidates flash as soon as it gets to the point where it's erasing flash pages.
I have had virtually no success with this with watches so far - maybe it's a language barrier thing, but the only way Bangle.js 2 works is because it's got the programming pins on the rear so we can program it here. I don't even have the schematics for the device - everything has had to be reverse engineered. It's not to say you shouldn't try though! You might get lucky. There's also a miniscule possibility that the SWD programming pins are actually available on the device somewhere - either on the outside, or on test pads that you could get to by drilling small holes in the case and filling them after (but I guess you'd only find that out by dismantling/destroying one first). |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-22 by user149759 Cool. I am willing to sacrifice one. I will try to order them this week. So, if I understand correctly, if the SWD pins are available, we can reprogram it right. My main interest is the heart rate sensor and getting raw values. The link I shared in the OP has HX3605 (I hope it has the drivers), I am not sure about the optical sensor in the second link. I will search for devices with HX3605 and try to place order. |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-23 by @fanoush Cool, let us know when you get it and what is its bluetooth name. We may already have its firmware and could tell if it is nrf52 inside. Some aliexpress listings even allow to return for free, not this cheap one though. I think hx3605 is used in Magic3/Rock/C6/C17/QY03 watches(?), getting raw data should not be big problem. |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-23 by @fanoush btw in this listing https://www.aliexpress.com/item/1005006527342041.html which is not nrf chip it can be seen that some of them are actually transparent so you can really see where the chips are. This one is said to be FR8016HA |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-02-23 by @gfwilliams That's cool! If you can find a transparent one you might even be able to see the test points for SWD. |
Beta Was this translation helpful? Give feedback.
-
|
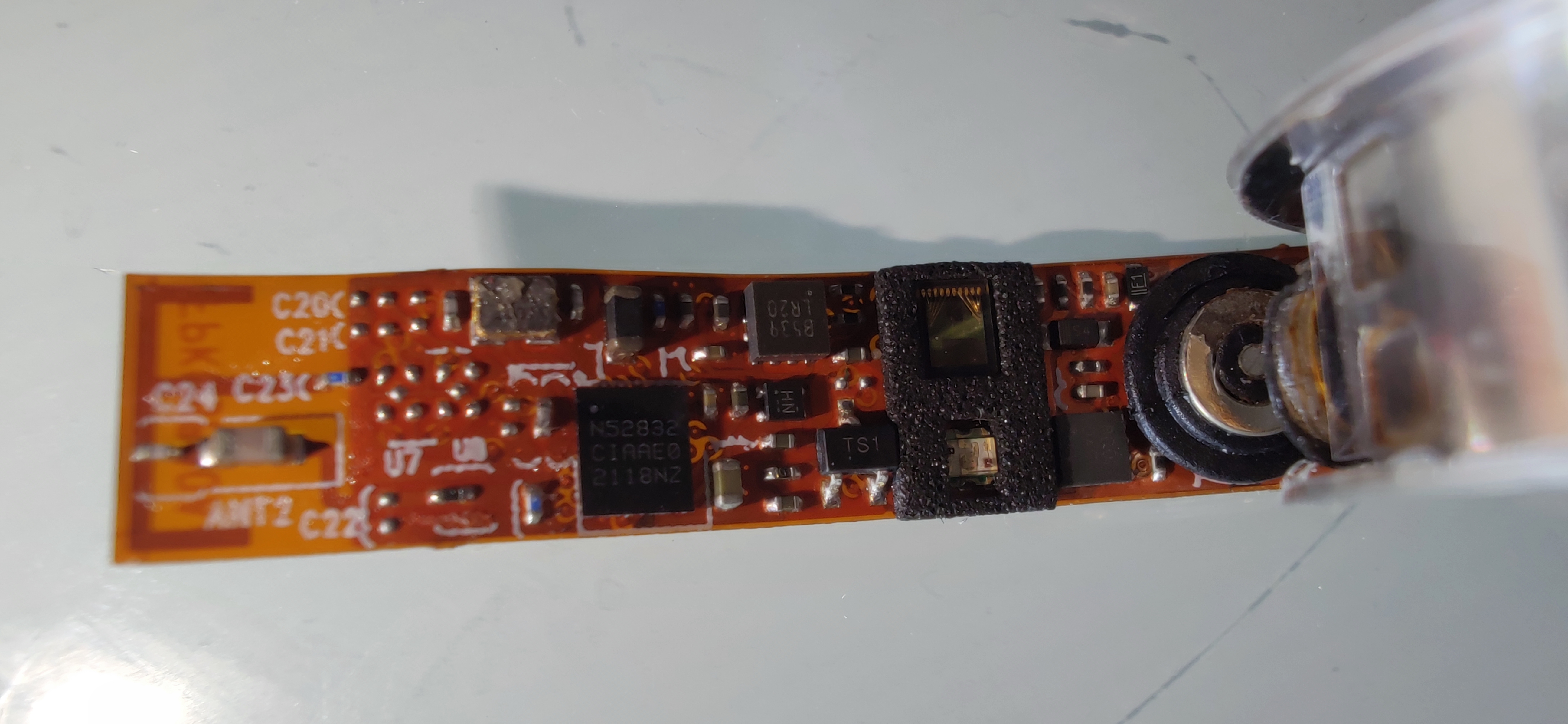
Posted at 2024-03-07 by user157679 Hi guys. After analyzing the Bluetooth requests, I've developed an ESP32 code as well as a Python code that reads the accelerometer values (they are sent over BLE only ~1/sec unfortunately, so nothing really usable for actions). Besides that, I couldn't do much more. I can't update the firmware as the seller never gave it to me and it is nowhere to be found on the Internet. So yesterday after reading this post, I thought **** it, let's crack it open. I'm attaching detailed pictures. Also, it seems that by slightly unbending the flex PCB, I created a bad contact of some sort as my ring was turning on and off, and now not even on.. working on it 🤞 Any help would be much appreciated 😁
|
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-03-07 by @gfwilliams That's really cool! So looking at that, I'd say that most likely the pads on the pack marked Some info at:
However it's super likely that the chip itself has had the software protection bits flashed, which means you can't read the code out. Although ATC1441 did have a hack for that using an ESP32 which you could give a try: https://github.com/atc1441/ESP32_nRF52_SWD But if that fails you'll just have to do the recovery over SWD (which wipes everything) and start from scratch. I'm not sure if @fanoush has written anything up on it, but you can flash a minimal Espruino firmware and then start messing with various wires (D0..D31) and see if you can figure out what's connected to what (but if you could get the firmware off it you could start to disassemble it and figure out which pins go where and what all the sensors are) The good news about it I guess is that if you had a 'new' ring, it looks like you could cut a small section out of the cover and get to the |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-03-07 by @fanoush
What is bluetooth name of that device and what is the name of android mobile app for it? If it is that VWAR ring and the name is R1 or R2 then maybe we have matching DFU zip. Also is there some firmware version info in the mobile app? EDIT: attached is some random nrf52 ring firmware, if the name is matching you may try DFU, either it will be refused or it will brick your device or it will still work. If it will still work then it can be later restored to it (over swd pins). Also the binary can be reverse engineered to get more info about the hardware.Attachments: |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-03-08 by user157679 @gfwilliams thanks for all the advice and information. I'll try to make some time and try with my ST-LINK and/or the ESP32 method whenever possible. Great idea for drilling holes through the cover for new rings. @fanoush where did you find those firmwares? |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-03-08 by @gfwilliams @user157679 thanks! I appreciate it! |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-03-08 by @fanoush
Well, it is from Smart Health app - firmware update functionality available from their servers, sadly there is no firmware file named R8, btw is b8:37 part of your device mac address? I'll search other binaries for R8 maybe the file has different name. EDIT: searched all binaries and sadly don't see any with "R8" inside. for R1 and R2 the name is probably done in same way as there is this in the binary |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-06-03 by user158283 Can you share the details on how you captured the requests going from the app to the ring over BLE and also if possible share the python scripts for others to find it useful ? |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-06-18 by @fanoush Slightly related, not NRF but hackable https://hackaday.com/2024/06/16/new-part-day-a-hackable-smart-ring/ |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-06-19 by @gfwilliams I know - I spotted that post too! Porting something barebones is probably not too painful as you say. A version of the VCare sensor is in Bangle.js 2 so it's hopefully not that hard to support (although VCare never seem to publicly share info so I had to reverse engineer a lot of ours) I'm always interested in cheap Bluetooth chips - so if we were able to get hold of the "BlueX Micro RF03" separately such that I could actually use them on my boards, I'd be a lot more motivated to put some time into a port ;) If the RF03 bootloader is completely unsecure, it could actually be a good target as it'll mean that any devices with it in are dead easy to reflash. Having said that, if enough people were actually interested I might be able to get a manufacturer of an nRF52 based ring to flash Espruino firmware on to them (or at least an unlocked bootloader) at the factory - and that's likely a better long term option as the nRF52 is so well supported at the moment. |
Beta Was this translation helpful? Give feedback.
-
|
Posted at 2024-06-20 by adminy any updates @user157679 ? |
Beta Was this translation helpful? Give feedback.


-
Posted at 2024-02-21 by user149759
Hi everyone,
Has anyone started hacking a smart ring similar to smart watches. They have more or less same hardware like the other smart watches that are running the Espruino software.
https://www.aliexpress.us/item/1005006282241664.html?spm=a2g0o.productlist.main.15.438c4590tQY3B7&algo_pvid=990cea21-0763-43dd-a321-924f8c221ffa&algo_exp_id=990cea21-0763-43dd-a321-924f8c221ffa-7&pdp_npi=4%40dis%21EUR%2159.33%2150.43%21%21%21451.16%21383.49%21%402103297417085441338983843ebfb6%2112000036598148172%21sea%21IE%21913614891%21AC&curPageLogUid=7tKLHs6ULpmY&utparam-url=scene%3Asearch%7Cquery_from%3A
Beta Was this translation helpful? Give feedback.
All reactions